Category: advisory
-

December 22: Phishing Resistant Part 2: Synced Passkeys and the Economics of Recovery
Covers the risks of synced passkeys and efficient and secure account recovery,
-

December 2: Phishing Resistant Part 1: Helpdesk Vulnerable and the Truth About Synced Passkeys
Amateurs hack systems. Professionals hack people. Bruce Schneier 2025.12.21 Update: I have updated the technical guidance in Footnote 1 regarding Temporary Access Pass (TAP) support in Conditional Access policies. The recommended approach removes two manual steps from the typical recovery process and ensures continuous phishing-resistant enforcement during recovery. This is Part 1 of a series…
-

November 13: How To Do Teams Collab in GCC High
Just because it has a saddle, doesn’t mean you should ride it. Unknown Previously: How to configure cross-cloud Teams collaboration for B2B Guests. Below: How External Access, Cross-Cloud Meeting Join, and B2B fit together. Many GCC High applications and features are not supported or are limited. This article specifically focuses on the limitations of Teams…
-
November 11: How To Use GCC High For CMMC
All roads lead to Rome. Alain deLille When it comes to meeting CMMC requirements, every Defense Industrial Base (DIB) organization’s journey looks a little different, but most follow one of three main roads to compliance in GCC High. 1. Split Organization (Some Users Move to GCC High) This approach is popular among companies that handle…
-
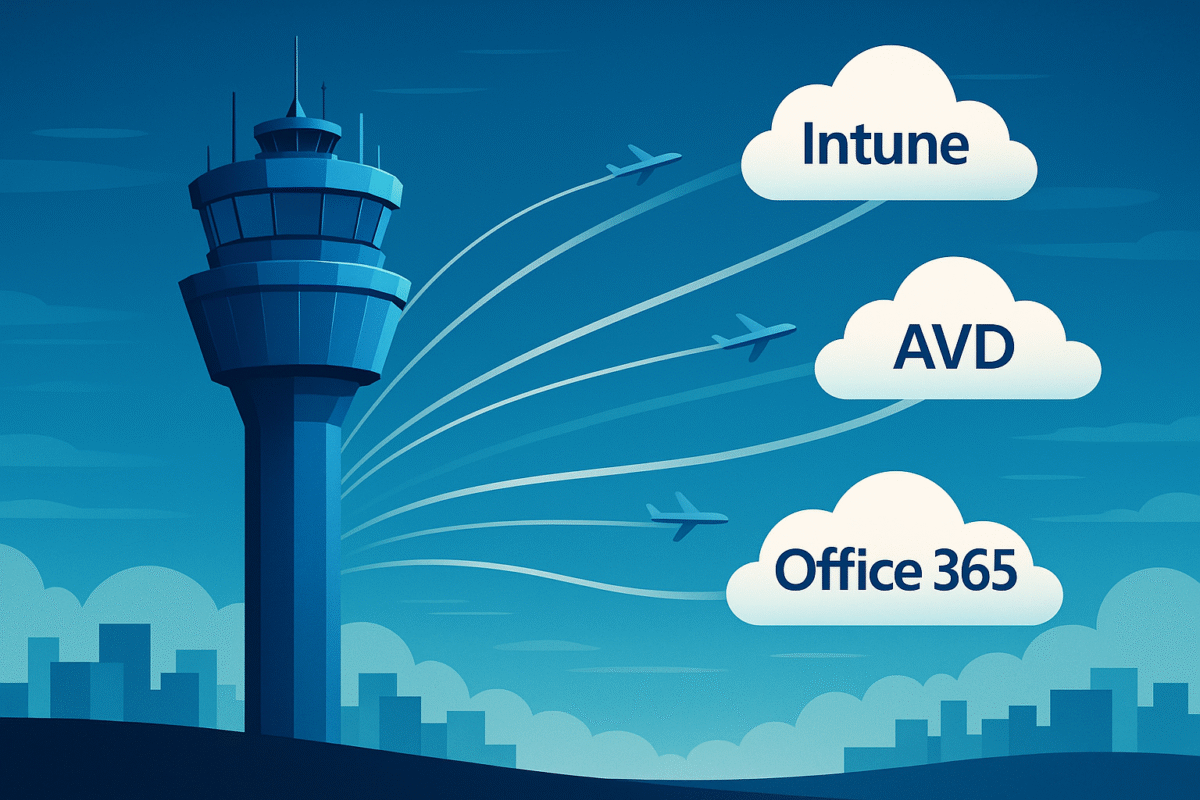
November 10: How To Manage the Azure Firewall in GCC High
Perfection is achieved, not when there is nothing more to add, but when there is nothing left to take away. Antoine de Saint-Exupéry A set of Azure Virtual Desktops (AVDs) in GCC High, secured by Azure Firewall, can serve as a compliant enclave for safeguarding Controlled Unclassified Information (CUI) under CMMC. This post shows one…
-

November 8: How to Stop ChatGPT Hallucinating Microsoft Answers
Welcome to the desert of the real. Jean Baudrillard, Simulacra and Simulation As we spend more time working with large language models, it’s easy to confuse fluency with accuracy. ChatGPT “hallucinations” – confidently stated errors – can become massive time wasters. Avoiding these wild goose chases requires discipline and clear prompting. To reduce these errors,…
-
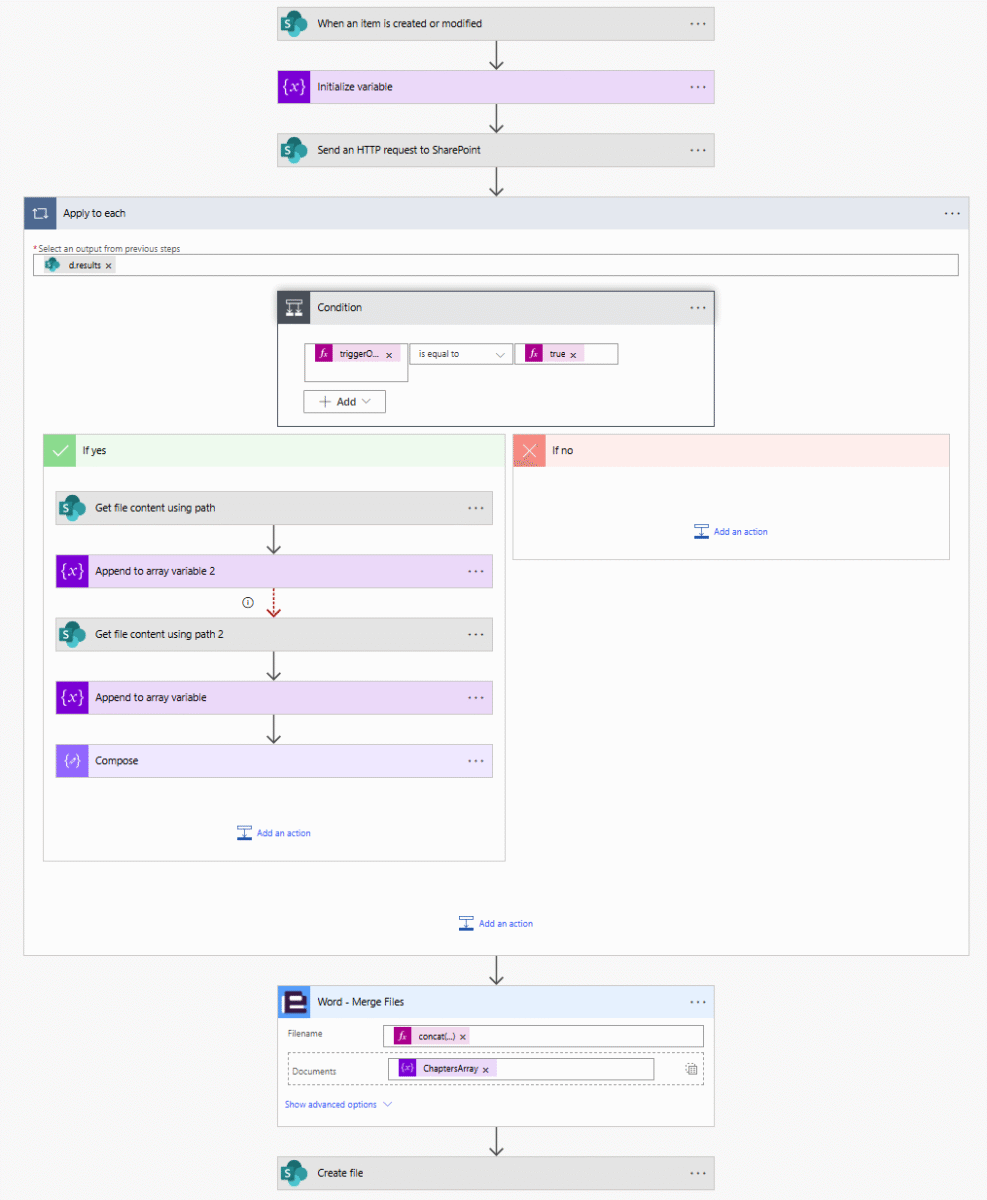
November 4: How To Automate Security Documentation
The best way to create a good habit is to automate it so you never have to think about it again. James Clear, Atomic Habits In my work helping clients secure their Microsoft cloud services, I learn something new almost every day. Undocumented quirks, easy-to-make mistakes, and hard-earned best practices rattle around my head like…
-
October 23: How to Disable Dangerous Entra Auth Methods
The best part is no part. Elon Musk 2025.11.04 Update: I’ve heard from a client that Microsoft sometimes tracks PSI with #microsoft.graph.microsoftAuthenticatorAuthenticationMethod. This may require removing all Authenticator auth methods to remove PSI. Stay tuned for how we address this… Authenticator Passwordless Phone Sign-In allows anyone who knows a user’s UPN to MFA-bomb them into…
-
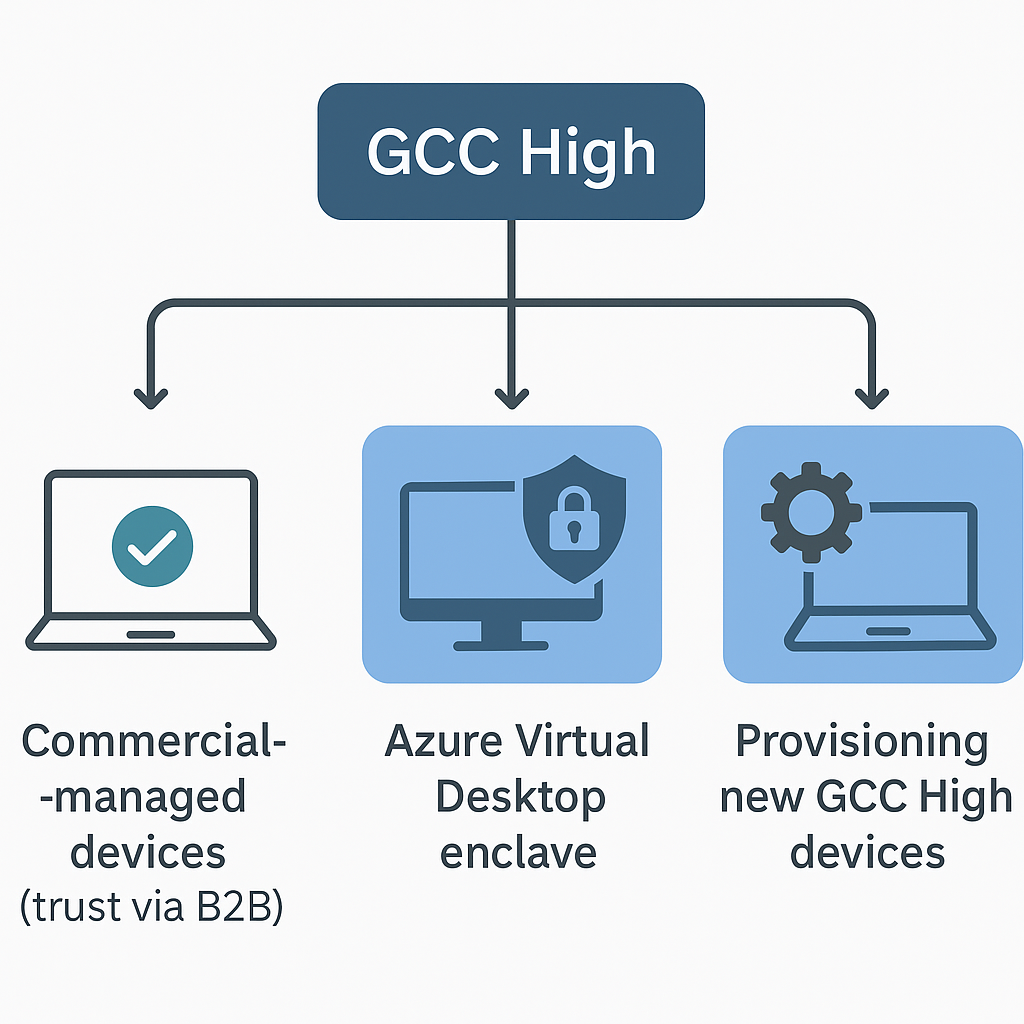
September 14: How To Manage Devices In GCC High
Trust, but verify. Ronald Reagan Government contractors moving to Microsoft 365 GCC High face unique device management challenges. IT directors and MSPs must balance compliance, user productivity, and simplicity. This post explores how organizations can manage devices for GCC High environments confidently – whether by leveraging existing Commercial cloud devices, creating a secure virtual enclave, or…
-
September 7: Simple, Reliable Cross-Cloud Teams Collab in GCC High
Less but better Dieter Rams Two years out of Microsoft, I’m more convinced than ever of the power of simple, coherent design. Cross-cloud collaboration between Commercial and GCC High offers many paths, but, in my experience, only one is worth your time — and even that path is strewn with small but critical quirks. I’ve…